Common misconceptions about IPv6 security | APNIC Blog
Misconceptions can be dangerous. This is especially true when they lead to network this post I’ll seek to set the record straight for several of the most common misconceptions about IPv6 security. IPv6 is more/less secure than IPv4There are two big misconceptions about IPv6 security:IPv6 is more secure than IPv4IPv6 is less secure than IPv4Neither are true. Both assume that comparing IPv6 security with IPv4 security is meaningful. It is ’s networks, whether they have IPv6 deployed in them or not, are largely IPv6 compatible. All modern operating systems and network devices employ IPv6 dual-stacks, in which IPv6 is turned on by default. Even if you have not actively deployed IPv6, your networks still have the combined vulnerability surface of IPv4 and erefore, comparing IPv4 security with IPv6 security is meaningless. They both have the vulnerabilities of IPv4 and IPv6. Every network should be secured for IPv4 and IPv6. Ideally, you should have done this well over a decade ago. IPv6 is IPv4 with longer addressesIn network security, it is crucial not to underestimate the scale of risks. The most common misconception that I have heard in my twenty years of working with IPv6 is that IPv6 is IPv4 with longer addresses. It is not. IPv6 is vastly different from IPv4, often in complex and subtle ways. Sometimes, what is best practice in IPv4 is the opposite of best practice in IPv6 misconceptions: It’s fake newsIt is not possible to list all the differences here. Instead, I will illustrate this using addressing. This is one area where superficially the difference between IPv4 and IPv6 appears obvious. However, not only are IPv6 addresses longer, they are also inherently different in attributes, types, structure and how they are used. For example:They have new attributes: length, scope and is normal for IPv6 interfaces to have multiple addresses. IPv6 addresses can change over lticast plays a crucial role in core IPv6 are a vast number of methods for assigning interface identifiers (the bottom 64 bits) IPv6 addresses are used and managed is hugely public addresses are is only addressing. IPv6 has many other differences both in things we are familiar with in IPv4 and in completely new protocols and features. All of these have security implications; the biggest being that staff will not appreciate the differences, and therefore the need, to secure give you a feel for the scope of the IPv6 vulnerability surface, I have included the figure below. Of course, it is not intended to compare IPv4 and IPv6 security (indeed IPv4 is included). However, it does illustrate that there are many new areas to consider, some of which are significant. Figure 1 — The IPv6 vulnerability makes IPv6 more secure than IPv4Internet Protocol Security (IPsec) was designed to provide network layer security (authentication and encryption). It was included as a mandatory feature in the IPv6 standards. Many believed, and some still believe, that this gives IPv6 an advantage over are two reasons why this is not the case. Firstly, while including IPsec functionality in the IPv6 stack was mandatory, using IPsec is not mandatory. Secondly, IPv4 also has IPsec, so there is no difference. Or is there? IPsec in IPv4 is often used for VPNs. These are terminated at the edge of networks. IPv4 IPsec is rarely used to secure end-to-end traffic. This is because of the widespread use of Network Address Translation in IPv4 (NAT44). NAT44 mangles the IPv4 headers and breaks IPsec. In IPv6 this restriction does not exist. Using IPsec end-to-end becomes more practical. IPv6 is already facilitating new and innovative ways of using IPsec. We have clients who are using IPv6 IPsec to secure all traffic within their data centres. We also have clients who have deployed IPv6 to leverage IPsec based end-to-end security allowing them to decommission their existing VPN dress scanning is impossible in IPv6The enormous number of IPv6 subnet addresses (264 = 18, 446, 744, 073, 709, 551, 616) is often thought to make it impossible for attackers to scan IPv6 subnets. There is some truth in this. To sequentially scan a gigabit ethernet subnet would take 491, 351 years if there is no other ever, it is not impossible for an attacker to find addresses in a subnet, it is simply harder. How hard depends on the type of addresses that you are using and where the scanner is Zesplot: visualizing IPv6 address spaceIf the network’s IPv6 addresses have a known structure, then scanning them becomes much easier. For example, some organizations number their hosts sequentially: for example, 1, 2, 3. This is the first sequence a scanner is likely to base their IPv6 address structure on IPv4 addresses. This is not considered to be a good idea. From a security perspective, it makes address scanning as trivial as it is in an IPv4 network. Even networks that use modified EUI-64 addresses that are based on MAC addresses can be scanned if an attacker has enough prior, the use of opaque static and privacy addresses can make remote IPv6 address scanning impractical. However, discovering addresses by other means may still be timating the time required to scan an IPv6 subnet: Length of Neighbour Solicitation frame (including the preamble and interframe gap) = 840 bitsTime to send Neighbour Solicitation on gigabit ethernet = 0. 00000084 secondsTime to transmit all 264 Neighbour Solicitation = 1. 54953 x 1013 seconds= 1. 54953 x 1013/31536000 = 491351. 6306 years(Assumes that there is no other traffic on the subnet! )No NAT makes IPv6 insecureOne of the most common misconceptions regarding IPv6 security is that the lack of NAT makes IPv6 less secure. NAT44 is often seen as a security feature in IPv4 networks. The use of public addresses in IPv6 and the restoration of end-to-end connectivity is of great concern to many IPv4 network nfusing brokenness with security is a mistake. Firewalls can easily provide equivalent and better protection than NAT without breaking end-to-end connectivity. Ironically, NAT44 and its associated myriad of NAT-traversal techniques have many security issues of their lessonsThese are just a few of the most common misconceptions about IPv6 security. There are many key lessons are:Don’t underestimate the scale of the differences between IPv6 and IPv4 networks need to be secured against IPv6 network and security staff need to be competent in IPv6 and in IPv6 security IPv6 is deployed will influence how secure it is in a longer introduction to IPv6 security threats and security features, watch my presentation at the UK IPv6 Council on IPv6 Security David Holder is CEO and chief consultant at Erion Ltd. He has over twenty years’ experience providing IPv6 consultancy and training to enterprises and organizations around the views expressed by the authors of this blog are their own
and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
Learn the Difference Between IPv4 and IPv6 – Parallels
October 21, 2020Last updated on June 1, 2021
The Internet Protocol, or IP, is the set of rules that makes it possible for our computers and other communication devices to connect to each other over the internet. Whenever you open a website on your browser, a data packet with your IP address is sent to the web server’s own IP address, after which the website is then served over the internet back to your device.
IPv4 and IPv6 stand for Internet Protocol version 4 and version 6, respectively. The two versions currently coexist, and IPv6 will take over once the IPv4 addresses run out. What are the major differences between IPv4 and IPv6? Let’s find out.
IPv4 Definition
IP addresses operate in the same way as street addresses laid out on a map. They direct packets to their intended destinations.
IP controls all internet traffic. Data packets with the IP information of their points of origin and their destinations travel on the internet, with routers helping to direct them down the correct path.
IP is the other half of TCP/IP, or the so-called Internet Protocol Suite. TCP, Transmission Control Protocol, governs the transport layer while IP is concerned with the network layer. TCP/IP was developed by the Defense Advanced Research Projects Agency (DARPA), a US federal agency under the Department of Defense. It became the computer networking standard for the US military in 1982. Soon after, it became the primary standard for packet-switching networks like the internet.
IPv4 is a connectionless protocol operating on a best-effort delivery model, which means it does not guarantee delivery nor can it avoid duplicates. TCP sits atop IP and addresses these shortcomings through mechanisms such as data integrity checking.
IPv4 became the main protocol governing data packet transmissions in 1981. During the definition of the standard, the version numbers progressed rapidly, starting with version 1 until IPv4 became the one that was utilized in ARPANET, the forerunner of the internet, in 1983.
Originally, IP addresses were designed to support only a low number of networks. By the time IPv4 was rolled out in 1981, it had been divided into address classes in a classful network addressing architecture to cope with this limitation. This architecture was superseded in 1993 when Classless Inter-Domain Routing (CIDR) was introduced to slow both IPv4 address exhaustion and the rapid growth of routing tables across the internet.
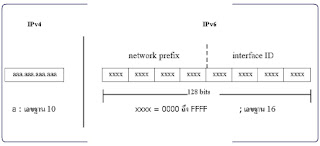
IPv4 addresses are numeric and formatted using dotted decimal notation, or four decimal octets separated by dots, e. g., 172. 217. 31. 238. Since an octet is eight bits in length, with the four octets, each IPv4 address is 32-bits, or four bytes, long.
At 232 IP addresses, the number of IPv4 addresses total almost 4. 3 billion. The number goes down to around four billion if some 300 million addresses reserved for multicast and private networks are excluded. Network address translation (NAT) is used to allow IP addresses reserved for private networks to communicate over the internet.
It was originally thought that IPv4 could provide IP addresses for all devices on the internet but it soon became apparent that a more robust alternative was needed to meet future demand, even if IPv4 addresses could be reused. With the number of devices accessing the internet already numbering in the billions, especially since smartphones and the Internet of Things (IoT) have become ubiquitous, almost all IPv4 addresses have been assigned—enter IPv6.
IPv6 Definition
As internet use took off in the 1990s, the Internet Engineering Task Force (IETF), the open standards body in charge of defining technical internet protocols, became aware of a potential problem in IPv4: The number of available IP addresses it can generate is limited and will not be enough to assign to devices accessing the internet in the foreseeable future.
The IETF decided that a better standard for future-proof IP addressing was needed. By 1998, it had come up with a draft standard for the better and improved IPv6, which was intended to supersede IPv4 eventually.
IPv6 provides for a 128-bit IP address. This means that it allows the generation of 2^128 or approximately 3. 4 × 10^38 addresses. In layman’s terms, the number of IPv6 addresses can be trillions of trillions.
Since IPv6 also reserves blocks of numbers for special use or excludes some numbers from use altogether, the actual number of IPv6 addresses should be slightly less, just like in IPv4. Still, the number of IPv6 addresses is virtually limitless and should be enough to meet future demand.
While IPv6 conforms to the same design principles as IPv4, IPv6 addresses come in eight groups of four hexadecimal digits, with each separated by colons such as fe80:0000:0000:0350:9804:1781:4371:2d03. The majority of IPv6 addresses don’t occupy all their 128 bits, leading to fields that contain only zeros or gets padded with zeros.
With IPv6 addressing architecture, you can use the two-colons (::)to represent a contiguous 16-bit field of zeros. For example, you can collapse fe80:0000:0000:0350:9804:1781:4371:2d03 into fe80::0350:9804:1781:4371:2d03 to make it more readable.
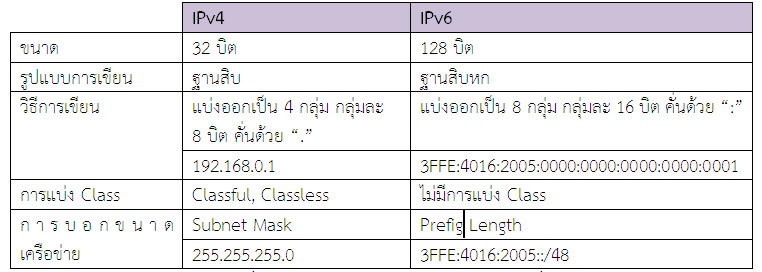
IPv4 and IPv6 Differences
Feature
IPv4
IPv6
Size of the address
32 bits
128 bits
Addressing method
IPv4 is a numeric address. It uses a dotted notation to
separate the binary octets.
IPv6 is an alphanumeric address. It uses a colon to
separate the binary bits.
Number of classes
There are five classes, A to E.
It allows a limitless number of IP addresses.
Type of addresses
Unicast, multicast, broadcast
Unicast, multicast, and anycast
Number of header fields
12
8
Length of header filed
20
40
Checksum fields
Has checksum fields
Has no checksum fields
Packet size
The minimum packet size for an IPv4 is 576 bytes.
The minimum packet size for an IPv4 is 1208 bytes.
Mapping
IPv4 uses the address resolution protocol (ARP) to map an
IP address to the media access control (MAC) address.
IPv6 uses the neighbor discovery protocol (NDP) to map the
IP to MAC address.
Dynamic host configuration server (DHCS)
Clients request the DHCSs’ for IP addresses before
connecting to the network.
Clients have permanent addresses. There is no need for
DHCSs.
Simple network management protocol (SNMP)
IPv4 uses SNMP for system management.
IPv6 does not use SNMP
Compatibility with mobile devices
IPv4 uses a dot-decimal notation, which is not appropriate
for mobile networks.
IPv6 uses hexadecimal colon-separated notation, which is
more appropriate for mobile networks.
Local subnet group management
IPv4 uses the internet group management protocol (GMP)
IPv6 uses multicast listener discovery (MLD).
Interoperability and mobility
It limits network topologies, therefore, hindering
interoperability and mobility.
It has interoperability and mobility capabilities embedded
in network devices.
Subnet mask
The designated network uses the subnet mask from the host
portion.
It does not use subnet masks.
Routing information protocol (RIP)
IPv4 supports RIP
IPv6 does not support RIP
Address features
IPv4 uses the network address translation (NAT) that allows
a single address to mask multiple non-routable addresses.
IPv6 uses direct addressing due to its vast address space.
Security
Security depends on the applications.
IPv6 has an internet protocol security (IPsec) built into
the protocol to provide automatic security.
Optional fields
Has optional fields
It has no optional fields. It offers extension headers.
The most significant difference between IPv4 and IPv6 is the virtually limitless number of IP addresses allowed in the latter. When IPv4 came out, mobile devices were not yet common. Thus, IPv4 was built without mobile networks and IoT-enabled devices in mind. When these devices go online and connect to the internet, they go through indirectly, via NAT. This process can sometimes pose problems for IPv4 devices.
With mobile device internet access now the standard, shifting to IPv6 is imperative, as it allows for more streamlined communications between devices. It is not surprising that mobile networks lead in the adoption of IPv6, given the advantages it offers them. IPv6 allows a single device to have multiple IP addresses depending on how that device is used. Instead of going through NAT, each device connects directly to the internet using its own assigned IP address.
When IPv4 came out, network security was not yet anyone’s foremost concern. However, IPv4’s updates allow it to be configured with the same IP security standards as IPv6. Although IPv6 is designed to be more secure with its built-in encryption capabilities and packet integrity checking, IPv4 can also be made more secure so there is essentially no difference between them when it comes to Internet Protocol security (IPsec).
However, IPv4 requires Address Resolution Protocol (ARP) to map to a device’s physical, or media access control (MAC), address. ARP is prone to spoofing and can be a vector for man-in-the-middle or denial-of-service attacks on a network. Although this risk can be mitigated by using software designed to prevent such attacks, it nevertheless poses a problem.
To map to a device’s MAC address, IPv6 uses the more robust Neighbor Discovery Protocol (NDP) and its related extensions, including Secure Neighbor Discovery Protocol (SEND), a security extension that provides cryptographic addresses and a public key infrastructure (PKI) separate from the IPsec inherent in IPv6. Thus, despite IP security presence in IPv4, there remains a difference between IPv4 and IPv6, security-wise.
As for device configuration, IPv4 may either require extensive manual configuration or assisted configuration using Dynamic Host Configuration Protocol (DHCP). In contrast, autoconfiguration is available for each device with an IPv6 address. Again, IPv6 wins hands down when it comes to device configuration.
Since it has matured and improved through the years, IPv4 performs at speeds up to par with IPv6, which is theoretically faster since it does not require NAT. However, IPv6 network performance should surpass IPv4 networks soon, as network administrators become more adept in optimizing them like they have learned to tune IPv4 networks.
IPv6 Pros and Cons
The danger of eventually running out of IP addresses has passed because of IPv6. However, the larger number of addresses in IPv6 is not the only advantage it has over IPv4.
For one, hierarchical address allocation in IPv6 addresses the increasingly complex routing tables in IPv4, an issue that had been addressed previously through CIDR. IPv6 addressing is straightforward and does not pose a problem for routers. With IPv6, CIDR is no longer essential, though you can still use it for router configuration.
Moreover, IPv6 has a new packet format that is designed to undergo minimal router processing. Thus, IPv6 should make for easier network management, more efficient routing and better device mobility. However, since the packet format for IPv6 is different from that of IPv4, the two IP standards are not interoperable. The IETF has tried to mitigate the potential issues arising from this non-interoperability; so far, these measures have proven successful in ensuring that both standards can operate together without any major issues.
Another area where IPv6 holds an edge is multicast addressing, which allows devices to send bandwidth-intensive packets such as multimedia streams to multiple destinations simultaneously.
IPv6 also provides for easier configuration. It allows simultaneous connections to multiple networks, which is not possible with IPv4. While IPv6 can still use static IP addresses or DHCP, it can utilize stateless automatic configuration. This allows seamless integration with prefixes and routers on the network and at the same time gives IPv6 devices the capability to assign addresses automatically to themselves using a unique 64-bit identifier. This auto-configuration capability is why IPv6 is ideal for use in IoT-enabled devices.
Other benefits of IPv6 include better security out of the box. With IPv6, ping scans are no longer needed, taking away a potential vector for worms to spread across your network. On the minus side, this leaves DNS servers as potential targets for attackers.
Other cons of IPv6 include the need to upgrade networking devices that are not designed for IPv6.
It may also prove difficult to type and remember overly long IPv6 addresses composed of letters and numbers and fit them in network topology diagrams. Although this sounds trivial, it may prove to be difficult and bothersome if you are administering large networks. You also must remember to enable IPv6 routing and disable IPv4 routing at the same time when you start moving to IPv6.
Migration from IPv4 to IPv6 may prove complicated, given that the two protocols are not backward compatible. This may mean assigning new IP addresses manually at the start. This process should become less problematic as networks eventually transition to IPv6.
To minimize costs when moving to IPv6, companies can adopt a strategy that would allow them to leverage their current IPv4 infrastructure while taking advantage of the benefits offered by IPv6. Instead of totally replacing IPv4 with IPv6, you can opt to have a dual-stack network where your hardware runs on both protocols, using IPv6 when possible. This approach is feasible since it is supported by major vendors.
IPv6 Adoption
While IPv4 and IPv6 coexist right now, they are not designed to be interoperable. The IETF has several strategies in place to ensure that both protocols can exist together while preparing for the transition to IPv6. These allow IPv4 and IPv6 hosts to communicate with each other. Eventually, IPv6 addresses will become the norm, but that may still take a few more years.
While the anticipated total shift to IPv6 has yet to occur, internet registries around the world are already running out of IPv4 addresses. The biggest factor behind the slow adoption of IPv6 is the NAT, which allows the relatively narrow range of private IPv4 addresses to be used over the public internet. With NAT providing a workaround for the limited number of IPv4 addresses, corporate networks have not moved hastily towards IPv6.
Thus, the transition towards IPv6 has been slow. Although deployment of IPv6 started in 2006, IPv6 itself only became an official internet standard in 2017.
With internet registries sounding the alarm, IPv6 is now poised to take center stage in the IP-addressing space. Although it had more than two decades to mature, it has gained widespread traction in recent years.
Mobile networks, followed closely by internet service providers (ISPs), lead adoption of IPv6. Major websites have started transitioning to IPv6 as well. Trailing at the back are enterprises, hampered by their existing investments in IPv4 networks.
Problems encountered when migrating to IPv6 make matters worse for IPv6 adoption. For example, a Windows 10 bug related to IPv6 delayed Microsoft’s efforts to transition to IPv6 at its Seattle headquarters in 2017.
IPv4 will probably linger around for a few more years, or even another decade, as IPv4 equipment is expensive to replace. That is not to say that you should not adopt IPv6. Your organization should start moving towards IPv6 adoption to avoid any major issues later.
Parallels RAS is IPv6 Compliant
Parallels® Remote Application Server (RAS) is IPv6-compliant and maintains backward compatibility with IPv4. It supports various deployment models, from on-premises to public cloud to a mix of the two and even hyper-converged deployment.
Parallels RAS allows quick creation of a virtual desktop infrastructure (VDI) with improved security and centralized desktop management capabilities. It offers support for various hypervisors and can facilitate automatic deployment of VDI desktops on-demand through custom guest virtual machine (VM) templates.
Parallels RAS supports a multi-tenant architecture through its own Tenant Broker, allowing different tenants to share Parallels Secure Client Gateways and High Availability Load Balancers while maintaining security and usage efficiency and lowering ownership costs.
Parallels RAS also provides Security Assertion Markup Language single sign-on (SAML SSO) integration, allowing centralized access to hosted resources. It even supports third-party load balancers such as Amazon Web Services Elastic Load Balancing services.
From the Parallels RAS Console, your administrators can configure a Parallels RAS farm, deploy servers, publish applications and desktops, monitor resources, manage connected devices and define security policies using a single pane of glass. These capabilities are also available on a web-based console, which can be served from any HTML5-compliant web browser. Get started with an IPv6-compliant VDI by downloading the Parallels RAS trial.
Get started with an IPv6-compliant VDI by downloading the Parallels RAS trial.
References
Wikipedia
IPv6 Security Myth #2 – IPv6 Has Security Designed In – Internet Society
Today we continue with part 2 of the 10 part series on IPv6 Security Myths by debunking one of the myths I overhear people propagating out loud far too much: That you don’t need to worry about security because IPv6 has it built into the protocol. In this post, we’ll explore several of the reasons that this is in fact a myth and look at some harsh realities surrounding IPv6 security.
Myth: IPv6 Has Security Designed In
Reality: IPv6 was Designed 15-20 Years Ago
The IPv6 protocol was primarily developed in the late 1990’s. In fact, RFC 2460, the “Internet Protocol, Version 6 (IPv6) Specification” is dated December 1998. This was a time when the commercial Internet had just started to flourish; security threats at this time were not anywhere near the sophistication and scale of threats common today.
While updates have been made to the protocol since 1998, the bottom line remains that relying on developers working well over a decade ago to protect you from security threats today and into the future is simply irresponsible.
This is the point where someone invariably points out that IPv6 requires IPsec (Internet Protocol Security), but…
Reality: IPsec is Not New
IPsec, which provides end-to-end per-packet IP layer authentication and encryption, has worked with both IPv6 and IPv4 since it was first standardized in RFC2401. This means that IPsec exists for IPv4 and that deploying it in IPv6 brings feature parity, not necessarily an enhancement.
The fact that IPv6 requires IPsec does mean that it’s available for use on all IPv6 capable devices, which is a step up over IPv4. It does not, however, guarantee the use of IPsec, which is what actually provides security. The responsibility remains with the application developer, the systems administrator, and the end user to actively apply IPsec for authentication and encryption.
[Correction 26 January: IPv6 no longer requires IPsec. Section 11 of RFC 6434, which obsoletes RFC 4292 on IPv6 Node Requirements, now states that IPsec SHOULD be supported (vs. the previous MUST). When I speak on this topic I usually point out that IPsec was required when many devices and applications with existing IPv6 support implemented it and that new implementations are still recommended to include IPsec support. These two facts combine to mean that although IPsec is no longer strictly required in every IPv6 node, it is still generally available pretty much everywhere it would be useful. The fact remains:]
You must actively use IPsec for it to provide any security whatsoever.
Reality: Extension Headers are Designed In
In order to make IPv6 as simple and interoperable as possible, it uses a minimalist standard packet header. In order to make IPv6 as extensible as possible, it allows “extension headers, ” additional chunks of meta-data that can be strung behind the IP header to provide additional features and functionality. IPsec leverages the extension header mechanism to carry necessary authentication and encryption data, for one example.
Unfortunately, having extension headers designed into the protocol for extensibility also means having security flaws designed in along with them.
Reality: Source Routing was Designed In
The first example of this is Routing Header Type 0 (RH0), which is an extension header that facilitates source routing. That is, allowing the sender to determine the path the packet takes across the network, rather than allowing the routers to route the packet naturally.
This functionality can be abused. For example you could potentially “program” a packet, or a string of packets, to “bounce” back and forth between two routers – potentially exhausting the available bandwidth on that link. Luckily, this threat was identified and RH0 was deprecated in RFC 5095:
The functionality provided by IPv6’s Type 0 Routing Header can be exploited in order to achieve traffic amplification over a remote path for the purposes of generating denial-of-service traffic.
Although RH0 has been deprecated, there is always a chance of older or unpatched networking gear being affected by a source routing attack using RH0. Therefor, you should always discard packets using RH0, and any other extension headers that may be deprecated in the future as well.
Reality: The Hop-by-Hop Option Header is Designed In
Another potentially problematic extension header is the Hop-by-Hop option header. As the name implies, this header is intended to provide options at every hop along the packet’s path. In other words, every IPv6 node that inspects, routes, or otherwise looks at the IP header must process the Hop-by-Hop option header. Most interestingly, perhaps, is that the Hop-by-Hop option header is generic and is designed to be filled with sub options, or TLVs (Type-Length-Values). These TLVs are unrestricted and unlimited, meaning you can stuff virtually any amount of virtually any data into the Hop-by-Hop option header.
In sum, this means that the Hop-by-Hop option header can be used to pull off an effective low-bandwidth Denial of Service (DoS) attack. The threat is detailed in an expired IETF Internet Draft, “The case against Hop-by-Hop options:”
The denial of service attack can be carried out by forming an IP datagram with a large number of TLV encoded options with random option type identifiers in the hop-by-hop options header.
This extension header has not been deprecated and may have valid uses on your network, so each network will need to deliberately decide how to mitigate this threat. Two popular options are discarding packets with the Hop-by-Hop header and rate-limiting packets with the Hop-by-Hop header, particularly when router CPE usage is high.
Reality: Extension Headers are Vulnerable in General
Beyond the two specific extension header types detailed above, there are vulnerabilities that come with using extension headers at all. Stuffing tons of bits into an unnaturally large header, adding multitudes of individual headers to a single packet, and using invalid extension headers are all methods of attack.
Because extension headers are part of the IP packet, they must be identified and dealt with by at least some of the nodes on any IPv6 path. This means that IPv6 routers, firewalls, and other networking devices can have their CPU and memory resources exhausted dealing with malicious extension headers.
Reality: Neighbor Discovery is Vulnerable to LAN Attacks
Another one of the major enhancements to IPv6 (beyond address length and header structure) is Neighbor Discovery (ND). ND basically replaces the smattering of ICMP and ARP used by IPv4 with a more comprehensive, unified approach.
Unfortunately, as you may have guessed, there are some potential vulnerabilities in ND. Due to its trusting, on-net focus, attackers who gain access to a victim’s Local Area Network (LAN) can use ND to attack other hosts on that LAN. Forged ND messages can be used to glean information about other hosts, re-direct traffic, renumber other hosts, and even intercept traffic or launch a man in the middle attack. ND can also be exploited
Rogue Router Advertisements (RAs) have the potential to be particularly problematic. That threat is detailed in RFC 6104:
However, unintended misconfigurations by users or administrators, or possibly malicious attacks on the network, may lead to bogus RAs being present, which in turn can cause operational problems for hosts on the network. In this document, we summarise the scenarios in which rogue RAs may be observed and present a list of possible solutions to the problem.
Your primary defense against most ND based attacks is preventing unauthorized LAN access (and misconfigurations) in the first place.
Reality: Neighbor Discovery is Vulnerable
There is another NDP attack that does not necessarily require LAN access (although it makes it much easier). Just like ARP tables in IPv4, IPv6 routers and switches must keep track of LAN hosts. This is all done with NDP in IPv6. The problem arises from the fact that IPv6 networks have many, many more addresses than many switches and routers have NDP entries, so firing off packets with random source and/or destination addresses can trivially flood many devices’ neighbor cache. This results in a form of DoS on the network under attack.
Because Secure Neighbor Discovery (SeND) is not widely implemented, possible mitigations include using devices that are not vulnerable, blocking the source of the malicious traffic, using subnets smaller than a /64 (this has it’s own complications currently), and/or using static NDP entries. Beyond that, we need to demand more NDP configuration knobs from our vendors, to provide more granular control (logging, limiting, policing).
Reality: Many Attacks have Nothing To Do with IP
Finally, with all of that said, it is crucial to remember that buffer overflows, database injections, cross-site scripting, phishing, SPAM, DNS amplification, and many more of the most common attacks happen at layers above, or below, the IP layer. In other words, many attacks are completely unaffected by which version of IP you are using.
The bottom line is that securing an IPv6 host or IPv6 network does not happen automagically. It takes the same forethought and diligence required to secure any valuable asset. We’d like to give you a head start in that process with our IPv6 security resources, part of the Deploy360 portal.
Read the full series of IPv6 Security Myths articles and visit our Start Here page to get started with IPv6 today!
Frequently Asked Questions about ipv6 vs ipv4 security
Does IPv6 provide better security?
IPv6 also supports more-secure name resolution. The Secure Neighbor Discovery (SEND) protocol is capable of enabling cryptographic confirmation that a host is who it claims to be at connection time. This renders Address Resolution Protocol (ARP) poisoning and other naming-based attacks more difficult.
What is the difference between IPv4 and IPv6 regarding security issue?
Although IPv6 is designed to be more secure with its built-in encryption capabilities and packet integrity checking, IPv4 can also be made more secure so there is essentially no difference between them when it comes to Internet Protocol security (IPsec).Oct 21, 2020
Is IPv6 bad for privacy?
The IPv6 Stateless Address Autoconfiguration can be considered inherently harmful for the privacy of the user.