What is a Proxy Server? How It Works & How to Use It | Fortinet
What Is a Proxy Server?
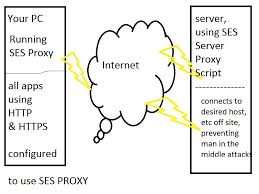
A proxy server provides a gateway between users and the internet. It is a server, referred to as an “intermediary” because it goes between end-users and the web pages they visit online.
When a computer connects to the internet, it uses an IP address. This is similar to your home’s street address, telling incoming data where to go and marking outgoing data with a return address for other devices to authenticate. A proxy server is essentially a computer on the internet that has an IP address of its own.
Proxy Servers and Network Security
Proxies provide a valuable layer of security for your computer. They can be set up as web filters or firewalls, protecting your computer from internet threats like malware.
This extra security is also valuable when coupled with a secure web gateway or other email security products. This way, you can filter traffic according to its level of safety or how much traffic your network—or individual computers—can handle.
How to use a proxy? Some people use proxies for personal purposes, such as hiding their location while watching movies online, for example. For a company, however, they can be used to accomplish several key tasks such as:
Improve security
Secure employees’ internet activity from people trying to snoop on them
Balance internet traffic to prevent crashes
Control the websites employees and staff access in the office
Save bandwidth by caching files or compressing incoming traffic
How a Proxy Works
Because a proxy server has its own IP address, it acts as a go-between for a computer and the internet. Your computer knows this address, and when you send a request on the internet, it is routed to the proxy, which then gets the response from the web server and forwards the data from the page to your computer’s browser, like Chrome, Safari, Firefox, or Microsoft Edge
How to Get a Proxy
There are hardware and software versions. Hardware connections sit between your network and the internet, where they get, send, and forward data from the web. Software proxies are typically hosted by a provider or reside in the cloud. You download and install an application on your computer that facilitates interaction with the proxy.
Often, a software proxy can be obtained for a monthly fee. Sometimes, they are free. The free versions tend to offer users fewer addresses and may only cover a few devices, while the paid proxies can meet the demands of a business with many devices.
How Is the Server Set Up?
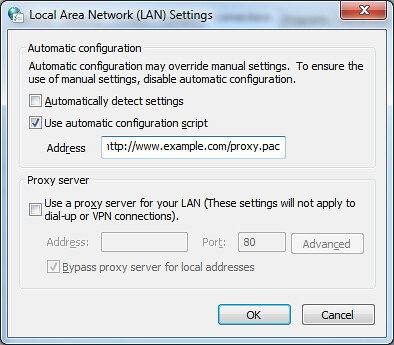
To get started with a proxy server, you have to configure it in your computer, device, or network. Each operating system has its own setup procedures, so check the steps required for your computer or network.
In most cases, however, setup means using an automatic configuration script. If you want to do it manually, there will be options to enter the IP address and the appropriate port.
How Does the Proxy Protect Computer Privacy and Data?
A proxy server performs the function of a firewall and filter. The end-user or a network administrator can choose a proxy designed to protect data and privacy. This examines the data going in and out of your computer or network. It then applies rules to prevent you from having to expose your digital address to the world. Only the proxy’s IP address is seen by hackers or other bad actors. Without your personal IP address, people on the internet do not have direct access to your personal data, schedules, apps, or files.
With it in place, web requests go to the proxy, which then reaches out and gets what you want from the internet. If the server has encryption capabilities, passwords and other personal data get an extra tier of protection.
Benefits of a Proxy Server
Proxies come with several benefits that can give your business an advantage:
Enhanced security: Can act like a firewall between your systems and the internet. Without them, hackers have easy access to your IP address, which they can use to infiltrate your computer or network.
Private browsing, watching, listening, and shopping: Use different proxies to help you avoid getting inundated with unwanted ads or the collection of IP-specific data.
Access to location-specific content: You can designate a proxy server with an address associated with another country. You can, in effect, make it look like you are in that country and gain full access to all the content computers in that country are allowed to interact with.
Prevent employees from browsing inappropriate or distracting sites: You can use it to block access to websites that run contrary to your organization’s principles. Also, you can block sites that typically end up distracting employees from important tasks. Some organizations block social media sites like Facebook and others to remove time-wasting temptations.
Types of Proxy Servers
While all proxy servers give users an alternate address with which to use the internet, there are several different kinds—each with its own features.
Forward Proxy
A forward proxy sits in front of clients and is used to get data to groups of users within an internal network. When a request is sent, the proxy server examines it to decide whether it should proceed with making a connection.
A forward proxy is best suited for internal networks that need a single point of entry. It provides IP address security for those in the network and allows for straightforward administrative control. However, a forward proxy may limit an organization’s ability to cater to the needs of individual end-users.
Transparent Proxy
A transparent proxy can give users an experience identical to what they would have if they were using their home computer. In that way, it is “transparent. ” They can also be “forced” on users, meaning they are connected without knowing it.
Transparent proxies are well-suited for companies that want to make use of a proxy without making employees aware they are using one. It carries the advantage of providing a seamless user experience. On the other hand, transparent proxies are more susceptible to certain security threats, such as SYN-flood denial-of-service attacks.
Anonymous Proxy
An anonymous proxy focuses on making internet activity untraceable. It works by accessing the internet on behalf of the user while hiding their identity and computer information.
A transparent proxy is best suited for users who want to have full anonymity while accessing the internet. While transparent proxies provide some of the best identity protection possible, they are not without drawbacks. Many view the use of transparent proxies as underhanded, and users sometimes face pushback or discrimination as a result.
High Anonymity Proxy
A high anonymity proxy is an anonymous proxy that takes anonymity one step further. It works by erasing your information before the proxy attempts to connect to the target site.
The server is best suited for users for whom anonymity is an absolute necessity, such as employees who do not want their activity traced back to the organization. On the downside, some of them, particularly the free ones, are decoys set up to trap users in order to access their personal information or data.
Distorting Proxy
A distorting proxy identifies itself as a proxy to a website but hides its own identity. It does this by changing its IP address to an incorrect one.
Distorting proxies are a good choice for people who want to hide their location while accessing the internet. This type of proxy can make it look like you are browsing from a specific country and give you the advantage of hiding not just your identity but that of the proxy, too. This means even if you are associated with the proxy, your identity is still secure. However, some websites automatically block distorting proxies, which could keep an end-user from accessing sites they need.
Data Center Proxy
Data center proxies are not affiliated with an internet service provider (ISP) but are provided by another corporation through a data center. The proxy server exists in a physical data center, and the user’s requests are routed through that server.
Data center proxies are a good choice for people who need quick response times and an inexpensive solution. They are therefore a good choice for people who need to gather intelligence on a person or organization very quickly. They carry the benefit of giving users the power to swiftly and inexpensively harvest data. On the other hand, they do not offer the highest level of anonymity, which may put users’ information or identity at risk.
Residential Proxy
A residential proxy gives you an IP address that belongs to a specific, physical device. All requests are then channeled through that device.
Residential proxies are well-suited for users who need to verify the ads that go on their website, so you can block cookies, suspicious or unwanted ads from competitors or bad actors. Residential proxies are more trustworthy than other proxy options. However, they often cost more money to use, so users should carefully analyze whether the benefits are worth the extra investment.
Public Proxy
A public proxy is accessible by anyone free of charge. It works by giving users access to its IP address, hiding their identity as they visit sites.
Public proxies are best suited for users for whom cost is a major concern and security and speed are not. Although they are free and easily accessible, they are often slow because they get bogged down with free users. When you use a public proxy, you also run an increased risk of having your information accessed by others on the internet.
Shared Proxy
Shared proxies are used by more than one user at once. They give you access to an IP address that may be shared by other people, and then you can surf the internet while appearing to browse from a location of your choice.
Shared proxies are a solid option for people who do not have a lot of money to spend and do not necessarily need a fast connection. The main advantage of a shared proxy is its low cost. Because they are shared by others, you may get blamed for someone else’s bad decisions, which could get you banned from a site.
SSL Proxy
A secure sockets layer (SSL) proxy provides decryption between the client and the server. As the data is encrypted in both directions, the proxy hides its existence from both the client and the server.
These proxies are best suited for organizations that need enhanced protection against threats that the SSL protocol reveals and stops. Because Google prefers servers that use SSL, an SSL proxy, when used in connection with a website, may help its search engine ranking. On the downside, content encrypted on an SSL proxy cannot be cached, so when visiting websites multiple times, you may experience slower performance than you would otherwise.
Rotating Proxy
A rotating proxy assigns a different IP address to each user that connects to it. As users connect, they are given an address that is unique from the device that connected before it.
Rotating proxies are ideal for users who need to do a lot of high-volume, continuous web scraping. They allow you to return to the same website again and again anonymously. However, you have to be careful when choosing rotating proxy services. Some of them contain public or shared proxies that could expose your data.
Reverse Proxy
Unlike a forward proxy, which sits in front of clients, a reverse proxy is positioned in front of web servers and forwards requests from a browser to the web servers. It works by intercepting requests from the user at the network edge of the web server. It then sends the requests to and receives replies from the origin server.
Reverse proxies are a strong option for popular websites that need to balance the load of many incoming requests. They can help an organization reduce bandwidth load because they act like another web server managing incoming requests. The downside is reverse proxies can potentially expose the HTTP server architecture if an attacker is able to penetrate it. This means network administrators may have to beef up or reposition their firewall if they are using a reverse proxy.
Proxy Server vs. VPN
On the surface, proxy servers and virtual private networks (VPNs) may seem interchangeable because they both route requests and responses through an external server. Both also allow you to access websites that would otherwise block the country you’re physically located in. However, VPNs provide better protection against hackers because they encrypt all traffic.
Choosing VPN or Proxy
If you need to constantly access the internet to send and receive data that should be encrypted or if your company has to reveal data you must hide from hackers and corporate spies, a VPN would be a better choice.
If an organization merely needs to allow its users to browse the internet anonymously, a proxy server may do the trick. This is the better solution if you simply want to know which websites team members are using or you want to make sure they have access to sites that block users from your country.
A VPN is better suited for business use because users usually need secure data transmission in both directions. Company information and personnel data can be very valuable in the wrong hands, and a VPN provides the encryption you need to keep it protected. For personal use where a breach would only affect you, a single user, a proxy server may be an adequate choice. You can also use both technologies simultaneously, particularly if you want to limit the websites that users within your network visit while also encrypting their communications.
How Fortinet Can Help
FortiGate has the capability of both proxies and VPNs. It shields users from data breaches that often happen with high-speed traffic and uses IPsec and SSL to enhance security. FortiGate also harnesses the power of the FortiASIC hardware accelerator to enhance performance without compromising privacy. Secure your network with FortiGate VPN and proxy capabilities. Contact us to learn more.
What Are the Benefits of Using a Proxy Server? – CactusVPN
Ever wondered if there are any worthwhile benefits to using proxy servers?
Well, as a matter of fact, there are a few decent advantages (but also drawbacks) you as an online user should consider when deciding whether or not to use such a service.
Table of contents
What Is a Proxy Server?
How Does a Proxy Server Work?
What Types of Proxy Servers Are There?
4 Benefits of Using Proxy Servers
How “Anonymous” Are Proxies?
What Are the Drawbacks of Using Proxy Servers?
“Can I Use Free Proxies? ”
CactusVPN – Our VPN Servers Also Double as Proxy Servers
But before we start discussing the benefits of a proxy server, you might want to learn what a proxy actually is and how it works. It will help you better understand the proxy server advantages too – among other things.
In case you’re already familiar with this kind of info, feel free to just skip ahead to the “4 Benefits of Using Proxy Servers” section.
A proxy server (usually known as a “proxy” or “application-level gateway”) is a server (either a computer or an application) that acts a gateway between a local network and a large-scale network.
An example of that would be a server acting as an intermediary between your computer and the Internet.
Proxy servers can usually be categorized as being:
Forward – The standard proxy category, Forward proxies are the intermediary between a computer and a wider verse – Reverse proxies are intermediaries between the web and a smaller group of servers. For instance, a Reverse proxy could act as a gateway between the Internet and a corporate LAN – Open proxies (also called “public proxies”) can be accessed by any online user. They are usually offered to the public free of charge.
Basically, a proxy server will act as an intermediary between a client and the server from which the client is requesting a certain service. It will take the client’s request, and perform it on their behalf.
Here’s a basic example: Say you want to use a proxy server to access a certain web page. The proxy will receive your request, and will do one of the following things:
It will analyze its local cache to see if it can find that particular web page. If it finds it, it will return it to you without having to forward your request to the the proxy doesn’t locate the web page in its local cache, will request that web page from the web. However, it will not use your IP to do it. Instead, the proxy will act as the client on your behalf, and use one of its own IP addresses. Once it gets the page, it will relate it to your original request, and forward the page back to you.
Of course, you as a user won’t really be aware of that process. To you, it will just seem like you are directly accessing a web page like normal.
Overall, these are the most common types of proxy servers you’re likely to encounter:
HTTP Proxy Servers
These proxy servers can interpret network traffic, so they are used to cache web pages and files, making it easier and faster for users to access them.
HTTP proxies can affect multiple connections at the same time without their speeds taking a serious hit. All that speed does come at a cost, though – namely a complete lack of encryption.
SSL Proxy Servers
Also known as HTTPS proxies, these proxies provide SSL (Secure Socket Layer) support for the connection between the sender and the receiver in order to secure it.
SSL proxies are less likely to get blocked by your ISP, as they use TCP port 443. If your ISP were to block that port, it’d mean they’d also block your ability to engage in online shopping or banking.
SOCKS Proxy Servers
Unlike an HTTP proxy, a SOCKS proxy doesn’t really bother with interpreting web traffic – it just passes it along.
SOCKS proxies are quite versatile since they can handle multiple types of traffic, like emails (SMTP and POP3), FTP (File Transfer Protocol – used for uploading files to servers), IRC (Internet Relay Chat), and even torrent traffic.
However, due to their popularity, SOCKS proxies tend to be a bit slower, as they are usually overcrowded. Still, they do provide some security, as they offer HTTPS support.
Web Proxies
Web proxies can normally be used inside your browser. They don’t require you to install any additional software. Connections can be either HTTP or HTTPS, so the level of security can vary.
One issue with web proxies is that they have trouble dealing with Java, JavaScript, and Flash scripts, and that they aren’t really able to properly display complex website layouts.
Transparent Proxies
These proxies don’t require any configuration on your part, but they mostly have basic uses – at least from the perspective of an online user.
Still, it’s worth mentioning them because it’s a good idea to understand how they can affect you. While Transparent proxies can be employed by businesses to authenticate users when signing in on their WiFi networks, they can also be used by ISPs to filter various online content.
Fortunately, bypassing Transparent proxies is not too difficult. All you need is an encrypted proxy or a VPN (Virtual Private Network).
1. Your IP Address Is Hidden
One of the best proxy server advantages – by using a proxy, the website you access will not be able to log your real IP address, as it will log the proxy server’s IP address instead. Yes, that means you’re somewhat anonymous when you browse online.
Don’t forget – your IP address can tell someone a lot about yourself, like what country and city you are from. Crafty cybercriminals can even go the extra mile and use your IP address to find out things like who your ISP is, what your zip code is, and even what street you live on.
How would a hacker get access to your IP address, you ask? Sadly, a data breach or leak on a website you visit could be enough for them to get their hands on this info.
So, something like this is definitely useful nowadays.
2. You Can Access Geo-Blocked or Restricted Content
Unfortunately, a lot of online content is actually hidden behind geo-restrictions – mostly because of network and copyright regulations.
But since a proxy server hides your IP address, websites can’t stop you from accessing them based on your geo-location.
A good example of that is using a proxy to access NOW TV outside the UK.
On top of that, you can also use a proxy server to bypass network restrictions at work or school – restrictions that would prevent you from accessing certain types of online content.
3. Load Times Might Be Reduced
This is tied to the fact that proxy servers can cache data. Basically, once they access certain web pages, they store them for later. When a cached page is requested, they can display it faster to the user.
But please keep in mind that this will only happen if the proxy server already has the web page you request in its local cache. If it doesn’t, it will have to request it from the Internet, and you might not experience faster load times in that case.
4. Malicious Websites Can Be Filtered Out
Another handy proxy server benefit is the fact that the admin can block users from accessing websites that might be dangerous.
It might sound counterintuitive at first, but consider this: If the admin knows a certain website contains malware or phishing links, he/she can prevent proxy users from accidentally or unknowingly accessing it.
There could also be a chance that if you were to land on a malicious website, any malware it might contain would infect the proxy instead of your device. Though, keep in mind that’s not a guarantee.
We have over 30 servers around the world, and all of them come with 1 gbps speeds and unlimited bandwidth. Besides just being VPN servers, you can also use them as proxy servers if you want.
If you’d rather get all the perks a proxy can offer, and enjoy peace of mind knowing your online browsing is surveillance-free, and that your personal data isn’t at risk (not even on public WiFi), you can always just use our VPN apps.
We don’t keep any logs, so you don’t have to worry about us keeping tabs on your connections to our servers.
Special Deal! Get CactusVPN for $3. 5/mo!
And once you do become a CactusVPN customer, we’ll still have your back with a 30-day money-back guarantee.
Save 64% Now
The advantages of using a proxy server are quite nice, but proxies don’t come without their drawbacks.
For one, they don’t really offer you the kind of “anonymity” people like to claim they do. In fact, the owner of a proxy will always know who you are because they can see your IP address.
Now, proxy servers can be rated according to the level of privacy they offer. Officially, they come in 3 levels – with level 1 being the best for privacy:
Level 3 – Transparent Proxies
Not to be confused with the previously-mentioned Transparent proxies, these proxy servers don’t really offer any privacy.
Why? Because they forward pretty much all info about you to the websites you access. Theoretically, your IP is hidden, but it can still show up in the request header that’s sent to the website.
Level 2 – Anonymous Proxies
Also called Distorting proxies, these proxy servers don’t reveal your IP address to the server you are connecting at all.
Still, it is worth noting that the server you connect to will know you are using a proxy to access it. How come? Because it seems that “anonymous” proxies actually identify themselves because they attach additional headers to the requests they send.
Level 1 – Elite Proxies
The best choice – Elite proxies will hide your IP address, and the websites you access will have no idea you are using a proxy to connect to them.
Just keep in mind that for all the privacy-focused benefits of Elite proxy servers, you might have to settle for slower connections because they are very popular with online users.
Proxy servers don’t exactly offer you top-notch online security. Sure, some proxies come with an SSL-type encryption, but that’s not as secure as it sounds. Plus, if you value your privacy, you might not be too happy to hear that the NSA can actually intercept and break SSL.
Also, if you don’t plan on using a web proxy service, you will likely have to configure the proxy connection on your own. It’s not extremely complicated, but it can get annoying and tiring if you need to switch server locations quite often.
Oh yeah, and you have to be extremely careful which provider you choose. Don’t forget – if you happen to access anything online via HTTP instead of HTTPS, the owner of the proxy would be able to monitor your activities – not to mention a provider can also block harmless websites if they want to.
Well, you could. They’re free after all, so what do you have to lose?
Quite a lot, actually. Here are just some reasons why you shouldn’t use a free proxy service:
A lot of free proxies are run by volunteers. While that’s admirable, it also means the service can be unstable, and go offline at random intervals. 79% of free proxies don’t use HTTPS, leaving you completely “naked” free proxies can modify static HTML and use modified JavaScript to inject ads into the have no way of trusting the proxy provider, as they theoretically make no money off of you, so they don’t have any responsibility towards turally, free proxies are often overcrowded, so you will likely deal with slow Internet connections.
So, ideally, you should opt for private proxies instead. Even better, you could add an extra layer of security by using a VPN service that offers proxy server access.
If you’re not sure why you should use a VPN instead of a proxy, consider this – a VPN already offers the same benefits as proxy servers, and – on top of that – uses strong encryption protocols, keeping you safer online than a proxy server.
That, and they are configured at a system levels, meaning you only need to set it up once to make sure all your online connections on a device are proxied through the VPN.
And before you ask, no – free VPNs aren’t ideal either.
About proxy servers – Indiana University Knowledge Base
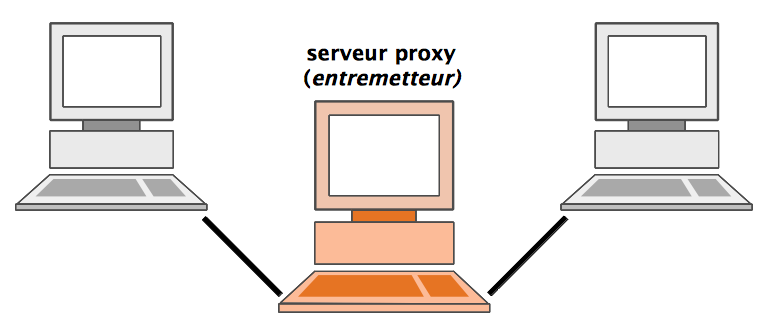
A proxy server, also known as a “proxy” or “application-level gateway”, is a computer that acts as a gateway between a local network (for example, all the computers at one company or in one building) and a larger-scale network such as the internet. Proxy servers provide increased performance and security. In some cases, they monitor employees’ use of outside resources.
A proxy server works by intercepting connections between sender and receiver. All incoming data enters through one port and is forwarded to the rest of the network via another port. By blocking direct access between two networks, proxy servers make it much more difficult for hackers to get internal addresses and details of a private network.
Some proxy servers are a group of applications or servers that block common internet services. For example, an HTTP proxy intercepts web access, and an SMTP proxy intercepts email. A proxy server uses a network addressing scheme to present one organization-wide IP address to the internet. The server funnels all user requests to the internet and returns responses to the appropriate users. In addition to restricting access from outside, this mechanism can prevent inside users from reaching specific internet resources (for example, certain websites). A proxy server can also be one of the components of a firewall.
Proxies may also cache web pages. Each time an internal user requests a URL from outside, a temporary copy is stored locally. The next time an internal user requests the same URL, the proxy can serve the local copy instead of retrieving the original across the network, improving performance.
Note:
Do not confuse a proxy server with a
NAT (Network Address Translation) device. A proxy server connects to, responds to, and receives traffic from the internet, acting on behalf of the client computer, while a NAT device transparently changes the origination address of traffic coming through it before passing it to the internet.
For those who understand the OSI (Open System Interconnection) model of networking, the technical difference between a proxy and a NAT is that the proxy server works on the transport layer (layer 4) or higher of the OSI model, whereas a NAT works on the network layer (layer 3).
This is document ahoo in the Knowledge Base.
Last modified on 2018-11-15 11:25:00.
Frequently Asked Questions about proxy server purpose
What are the 4 advantages of proxy servers?
4 Benefits of Using Proxy ServersYour IP Address Is Hidden. … You Can Access Geo-Blocked or Restricted Content. … Load Times Might Be Reduced. … Malicious Websites Can Be Filtered Out.Jun 25, 2018
What is an example of a proxy server?
Some proxy servers are a group of applications or servers that block common internet services. For example, an HTTP proxy intercepts web access, and an SMTP proxy intercepts email. A proxy server uses a network addressing scheme to present one organization-wide IP address to the internet.Nov 15, 2018
What is the main purpose of hacker to use a proxy server?
An attacker may use proxy hacking to gain an advantage over a competitor or, ultimately, to redirect users requesting the targeted page to a malicious or fraudulent website.