The Difference Between Proxy and Reverse Proxy | strongDM Many businesses use proxy servers to route and secure traffic between networks. There’s often confusion, however, on how this differs from a reverse proxy. In this post, we’ll dissect the two concepts and explain how administrators can use a reverse proxy […]
Tag: reverse proxy nginx
Reverse Proxy Firewall
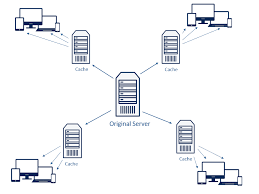
What is a Reverse Proxy Server? | NGINX A proxy server is a go‑between or intermediary server that forwards requests for content from multiple clients to different servers across the Internet. A reverse proxy server is a type of proxy server that typically sits behind the firewall in a private […]
Load Balancer And Reverse Proxy Together
What is a Reverse Proxy vs. Load Balancer? – NGINX Reverse proxy servers and load balancers are components in a client-server computing architecture. Both act as intermediaries in the communication between the clients and servers, performing functions that improve efficiency. They can be implemented as dedicated, purpose-built devices, but increasingly […]
Reverse Proxy Use Case
6 common use cases of Reverse Proxy scenarios | Packt Hub Proxy servers are used as intermediaries between a client and a website or online service. By routing traffic through a proxy server, users can disguise their geographic location and their IP address. Reverse proxies, in particular, can be configured […]
Reverse Proxy Attack
A fresh look on reverse proxy related attacks | Acunetix In recent years, several researches have been published about attacks deliberately or directly related to reverse proxies. While implementing various reverse-proxy checks on the scanner, I started analyzing implementations of reverse proxies. Initially, I wanted to analyze how both reverse […]
Forward And Reverse Proxy Server
The Difference Between Proxy and Reverse Proxy | strongDM Many businesses use proxy servers to route and secure traffic between networks. There’s often confusion, however, on how this differs from a reverse proxy. In this post, we’ll dissect the two concepts and explain how administrators can use a reverse proxy […]