Web proxies – SecTools Top Network Security Tools
Home
About/Help
Suggest a new tool
Top 125 Network Security Tools
For more than a decade, the Nmap
Project has been cataloguing the network security community’s
favorite tools. In 2011 this site became much more dynamic, offering
ratings, reviews, searching, sorting, and a new tool suggestion form.
This site allows open source and commercial tools on any platform,
except those tools that we maintain (such as the Nmap Security Scanner, Ncat network connector, and Nping packet manipulator).
We’re very impressed by the collective smarts of the security community and we highly recommend reading the whole list and investigating any tools you are unfamiliar with. Click any tool name for more details on that particular application, including the chance to read (and write) reviews. Many site elements are explained by tool tips if you hover your mouse over them. Enjoy!
4 tools
A Java-based web proxy for assessing web application vulnerability. It supports editing/viewing HTTP/HTTPS messages on-the-fly to change items such as cookies and form fields. It includes a web traffic recorder, web spider, hash calculator, and a scanner for testing common web application attacks such as SQL injection and cross-site scripting.
Read 6 reviews.
Latest release: version 3. 2. 13 on Aug. 8, 2006 (15 years, 2 months ago).
Fiddler is a Web Debugging Proxy which logs all HTTP(S) traffic between your computer and the Internet. Fiddler allows you to inspect all HTTP(S) traffic, set breakpoints, and “fiddle” with incoming or outgoing data. Fiddler includes a powerful event-based scripting subsystem, and can be extended using any language.
Read 4 reviews.
Latest release: version 4. 5. 1. 5 on July 23, 2015 (6 years, 3 months ago).
sslstrip is an SSL stripping proxy, designed to make unencrypted HTTP sessions look as much as possible like HTTPS sessions. It converts links to or to with a known private key. It even provides a padlock favicon for the illusion of a secure channel. Many HTTPS sites are normally accessed from a redirect on an HTTP page, and many users don’t notice when their connection isn’t upgraded.
Read 2 reviews.
Latest release: version 0. 7 on Dec. 18, 2009 (11 years, 10 months ago).
Ratproxy is a semi-automated, largely passive web application security audit tool. It is meant to complement active crawlers and manual proxies more commonly used for this task, and is optimized specifically for an accurate and sensitive detection, and automatic annotation, of potential problems and security-relevant design patterns based on the observation of existing, user-initiated traffic in complex web 2. 0 environments.
Review this tool.
Latest release: version 1. 58 beta on May 1, 2009 (12 years, 6 months ago).
Categories
Antimalware (3)
Application-specific scanners (3)
Web browser–related (4)
Encryption tools (8)
Debuggers (5)
Firewalls (2)
Forensics (4)
Fuzzers (4)
General-purpose tools (8)
Intrusion detection systems (6)
Packet crafting tools (6)
Password auditing (12)
Port scanners (4)
Rootkit detectors (5)
Security-oriented operating systems (5)
Packet sniffers (14)
Vulnerability exploitation tools (11)
Traffic monitoring tools (10)
Vulnerability scanners (11)
Web proxies (4)
Web vulnerability scanners (20)
Wireless tools (5)
What Is a Web Proxy and How Does It Work? | HideMyAss Blog
Home →
Access
→ What Is a Web Proxy and How Does It Work?
BlogPost 31567921702 What Is a Web Proxy and How Does It Work?
You’ve probably heard the term before, but what exactly is a web proxy? And how does it help you browse anonymously and access blocked content? Read on, and you’ll be sneaking around content blocks and hiding better than a chameleon in no time.
What is an anonymous web proxy?
Just to up the confusion factor on ya, there are a few similar, yet different terms we’re discussing here. So let’s get it straight before we move on:
A proxy server is a server that acts as an intermediary between your computer and the rest of the internet. Because you connect first to the proxy server, and then the proxy accesses your desired site on your behalf, you’re able to conceal your identity — which means hiding your IP address and geographic location.
A web proxy is a tool that facilitates your connection to a proxy server. Some sites offer a free web proxy to help you connect to their proxy server and browse anonymously.
A web proxy browser extension is like a web proxy, but it resides conveniently in your browser, so it’s always there whenever you want to use it.
How does a web proxy work?
Using a web proxy is pretty intuitive. First, type in the address of the free web proxy tool. Once you’re on the web proxy provider’s site, there will be a field where you can enter the website that you want to visit and select the server location you want to use. The web proxy then routes this request through your chosen proxy server.
The proxy server searches its cache of all the previous pages you’ve looked at. If it finds your current request in its memory, it’ll send it back to you without having to go onto the public internet.
If it doesn’t find it, the server will then use one of its own IP addresses to request the page you want to view. The website that hosts this page sees only your server’s IP address (not yours) and sends the page data to the server, which then forwards it on to you.
This process can happen so fast that it’s invisible, or there can be some noticeable delays, depending on the quality of the web proxy and how many people are using it. If you’re lucky, you wouldn’t even know that your computer had a stand-in if you hadn’t set it up yourself in the first place.
But using a web proxy tool does mean that you need to navigate to the tool’s website first every time you want to visit another site. It also means the proxy works only in that one tab. An easier solution is to download a web proxy extension, which sits conveniently in your browser. So it’s always there, ready and waiting anytime you need to hide your IP address or unblock a site due to content blocks, work restrictions, or any other reason.
How safe are web proxies?
It’s important to remember that nothing is 100% safe on the internet, and web proxies are no exception.
Many free proxies skimp on security and privacy features. If you’re considering using a free proxy tool, check and see if it uses encryption. If it doesn’t, then your internet traffic is an open book to hackers and advertisers. Unencrypted proxies are particularly unsafe to use on public Wi-Fi networks, since other people on the network can spy on your unprotected traffic with a little bit of hacker know-how.
Additionally, the proxy servers themselves may be vulnerable to hacking. If the administrators of the proxy server aren’t following basic cybersecurity standards, such as keeping their software up-to-date, then everything on those servers is up for grabs — and your IP address can be revealed to the world.
And while proxies block advertisers and your ISP (internet service provider) from seeing what you’re doing, the proxy server provider can see all your activity. That’s why it’s important to use a trustworthy proxy with a solid reputation and good user reviews.
HMA’s free proxy extension for Chrome or for Firefox encrypts your browser connection to protect your personal info. It sits conveniently in your browser, ready to provide anonymous browsing and ferry you around geographic content blocks anytime you need it. Choose from a variety of locations, then stream videos and download files easily.
Best uses of a free web proxy tool or extension
A free web proxy provides oodles of goodness:
Browse anonymously: Block your ISP, advertisers, and governments from seeing what you’re doing online.
Unblock geo-restricted content and avoid fees: Some streaming sites provide free content in one location, but charge a fee in another — or block access entirely. You can avoid that mess by using a proxy.
Surf faster: A proxy saves (“caches”) the sites you visit, which lets it load them very quickly the next time you return to the same site.
But remember that most free proxies only provide these benefits in a single tab that you need to navigate to every time you want to do anything. That’s why HMA’s free proxy browser extension is much more convenient, if we do say so ourselves.
What sites can you access with a proxy?
What can you access with a free web proxy? A better question might be, what can’t you access?! Social media, streaming platforms, news, sites blocked by geographic or work/school restrictions, sites of an “intimate” nature… go nuts!
That said, some sites may not work well with proxies. And some sites keep a list of IP addresses associated with proxy servers in order to block requests coming from those addresses if detected. That’s just one reason why a full VPN provides much more reliable results.
Isn’t a proxy just a VPN?
It sure isn’t! While proxies have some things in common with VPNs (virtual private networks), there are several important differences. A proxy is like a free light beer — it’ll get the job done, it’s free, and hey — it is still a beer! But if a proxy is a light beer, then a VPN is an expertly crafted cocktail, perfectly suited to your refined tastes.
How so? Well, for a start, a web proxy works only within your browser and nowhere else, which means it only anonymizes your web browsing. A VPN works on all kinds of devices, and encrypts your full connection to the internet. You can even put a VPN on your router so that all devices you have get VPN protection. And a VPN on mobile protects you any time you use your online banking app or other sensitive internet activity outside of a browser.
You can also use a VPN with a smart TV or use your Xbox over a VPN to get around content blocks and stream on the big screen.
A proxy is a quick and convenient solution to help unblock sites, but has pretty limited functionality. And if governments and companies really want to find out who you are, they can do so without too much trouble. So VPNs aren’t just for the next Edward Snowden — if you value your online privacy, VPNs make it much more difficult for would-be snoopers to track your activity across the web.
And VPNs — good ones, at least, like the expertly crafted cocktail that is the HMA VPN — provide tons of extra features. HMA VPN offers 1000 servers in 290 locations across 190 countries, servers that are optimized for streaming, protection against DNS leaks, 24/7 customer support, and more.
To dig deeper into the differences (and learn about one additional anonymous browsing option), check out our full review of Proxy vs. VPN vs. Smart DNS.
Browse privately with HMA
Ready to commit but still not sure if you should go with a proxy or a VPN? For the ultimate privacy and access experience, give HMA VPN a whirl. With our 30-day money-back guarantee, you can give it a spin risk-free.
Or head straight to our free web proxy extension to start browsing anonymously for the low, low price of zilch. You can choose HMA’s free proxy extension for Chrome or for Firefox to encrypt your browser connection and protect your super-sensitive data. Our proxy extension sits snugly in your browser, ready to carry you around geo-blocks anytime you need it. Choose from a variety of locations to stream videos and download files quickly and easily.
How To Configure And Use Charles Proxy On Windows and Android
Learn to Install, Configure and Use Charles Proxy – a Web Debugging Tool to Monitor the Network Traffic on Windows, Android and IOS Devices:
What Is Charles Proxy?
Charles Proxy is a web debugging tool that monitors the network calls and decrypts the web traffic.
It helps in understanding the content in your network call. E. g. Requests sent to the server and data fetched from the server etc. This network debugging tool can read the web traffic of Windows, Android and IOS devices.
What You Will Learn:Configuration Of Charles Proxy On Windows / Mac OSHow To Install Charles Proxy? Install Charles Root CertificateEnabling SSL ProxyingFeatures Of Charles ProxySaving And Sharing A SessionRemoving Charles CertificateConfiguration Of Charles Proxy On AndroidSteps To Configure Proxy On Android DeviceInstall Charles Root Certificate On Android MobileRemoving Charles Certificate On AndroidCharles Proxy Pricing – Subscription ModelFrequently Asked QuestionsConclusionRecommended Reading
Configuration Of Charles Proxy On Windows / Mac OS
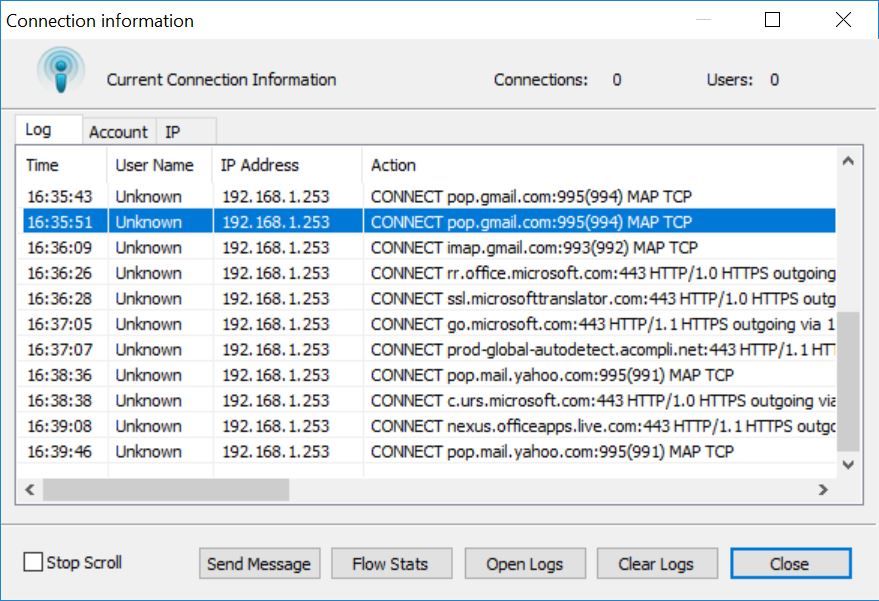
Charles Proxy sits between you & the server and monitors all network calls. For example, if you are searching for something on Google, then your machine should make a call to the Google server with the search query.
Charles acts as a mediator between you and Google and helps to monitor the server logs. These logs are very helpful when an application that needs a server is developed and tested.
How To Install Charles Proxy?
Open your browser and visit the download URL. You can find several download links for different OS versions i. e. Windows, Mac, and Linux OS versions.
The screen would look as shown below.
Click on the relevant link based on your OS. Download starts soon as you click on the link. Wait till the file downloads completely.
Go to your system’s Downloads folder where you will find an installer file with the name (version number may vary). Click on the file and a setup wizard will appear here.
Accept the license agreement and click on the Next button.
Click on the Finish button. Open the Charles application by clicking the shortcut icon.
The initial screen should look as shown below. The Windows proxy option will be enabled by default. You can check this by clicking on the proxy menu item at the top.
By default, the structure view will be enabled. You can see the logs getting recorded automatically.
Install Charles Root Certificate
#1) Click on the Help menu, and you can see the option “Install Charles Root Certificate” in the drop-down.
#2) Select the location Charles certificate to be installed i. current user/local machine.
#3) If you select the local machine, then you need to set the folder location by clicking on the browse button and select “Trusted Root Certification Authorities”.
#4) Click OK and continue with the installation process.
#5) In the end, you should see a popup saying that the certificate installation is successful.
Enabling SSL Proxying
Now you can use Charles for SSL proxying i. you can read a particular request made by your machine to your server.
For instance, open Google and type Wikipedia and search for it.
Open Charles proxy tool and shift to structure mode. You can see the display option (Sequence/Structure) at the top of the tool and click on the Structure mode.
In the filter editor provided, type wiki to search requests made particularly with this text.
Right Click on Google request end click on enable SSL proxying. Without enabling SSL proxying you will not be able to see the logs.
In this way, you can enable SSL proxying for a particular URL. If you want to monitor all the network calls, then you to need to configure a bit in the SSL proxying menu.
Follow the below steps to configure the SSL PRoxy Settings.
#1) Click on the Proxy menu item and click on SSL Proxy Settings.
There you can see that is already added in the list that was added in the previous step.
#2) Click on the Add button, and in the Edit location option add * in Host field and 443 in the Port field. Here * means anything, that the proxy tool will decrypt every URL.
Now, you are ready to read all the data from all the requests and responses.
Let’s explore the other features and components in the Charles proxy tool.
Right-click on any URL and you will see a list of available options. Most of them are straight forward and the name reflects the functionality
Features Of Charles Proxy
If you observe at the top of the proxy tool, you can see a ribbon with different buttons that have different functionalities.
Let’s dive deep into a brief description of each button.
#1) Clear Button: Upon clicking this button, the session will be cleared and after that, you can start a new session.
#2) Stop/Start Button: After launching the tool, by default, this button will be in ON mode. You can click on this button if you want to stop the log recordings.
#3) SSL Proxying: If you enable SSL proxying in settings as discussed in earlier sections, then this button will be turned on and you can stop SSL proxying at any time. Thereafter you can only see the traffic with limited data as SSL proxying is disabled.
#4) Network Throttling: Network throttling is to simulate different network bandwidth conditions like 2G, 3G, 4G, and WIFI. It can also be used to simulate customized modem network speeds.
It is useful when you have to test any application that has network dependencies or it will be useful to test how your application is behaving in different network conditions. You can customize the speed and other network conditions using keyboard shortcut Control+Shift+T or by clicking the Proxy menu => Throttle settings.
#5) Breakpoints: This feature does not help much unless you are developing an app. If you mark any request as a breakpoint, then the next time when Charles comes across this request, it waits for the user input asking the user to continue to the next point or to abort. This is similar to debugging code in Eclipse or Android Studio.
#6) Compose: Compose helps you to edit any request and send the edited request. You can edit/add any parameters and can execute to get the results for changed requests.
#7) Repeat Button: This button is to repeat a specific request. Once you click on this button, the request in the editor will be sent again. This feature comes handy when you want to recreate a request without performing the action again.
#8) Validate: Validate functionality is to validate the selected requests or responses. If you click on it, a new tab will be opened in the editor and you can see the validation results there.
#9) License Purchase: This button is used to purchase the license once the trial period is completed. For more details about purchasing a license, please visit the Subscription model section of this tutorial.
#10) Tools: This section contains different tools that help in debugging the traffic.
#11) Settings: The settings menu contains Access control settings, Proxy settings, Recording settings, Preferences, etc.
Saving And Sharing A Session
Consider a case where you are testing/debugging network calls related to an application and you need to share the logs with another tester/developer. You need to save or export the current session.
To save, just click Control+S keyboard shortcut or navigate to the File where you will find the Save option. Click on it and give an understandable name with as an extension, E. and hit the save button.
You can also Export the logs in the Files section and can save it in format. After this, you share the file to others. If you already have a log file in format, then you can import that file in the tool and can analyze the network traffic.
Removing Charles Certificate
While configuring the Charles proxy tool we installed Charles root certificate in the PC. Let’s see how to remove it when you don’t use it anymore.
#1) Search your PC for Certificate Manager. On Windows, it can be found with the name
#2) Once the certificate manager opens, click on Trusted Root Certification Authorities and then select the Certificates folder. After that, a list of certificates will be shown. Refer to the below screenshots for more clarifications.
#3) Right-click on Charles proxy certificate in the list shown and click on the Delete button.
#4) Click Yes on the confirmation dialog prompt. Now we have removed the Charles root certificate. Whenever you want to use Charles again, then you need to install a certificate.
Configuration Of Charles Proxy On Android
Charles Proxy tool supports Android devices as well. You can monitor the traffic of your Android device, from your PC. This needs some configuration in the WIFI settings of the Android device.
Your PC that has Charles installed and the Android device in which you want to check the logs should be connected to the same WIFI network.
If you have an idea about the configuration of a MITM proxy, then it will be easy for you to configure this setup. The process of installing certificates is almost similar in both the tools.
Steps To Configure Proxy On Android Device
#1) Open notification panel on mobile.
#2) Long click on the WIFI icon, then you will see advanced WIFI settings.
#3) On your PC, open command prompt or terminal and enter command ipconfig.
#4) There you can see your system IP address. Refer to the below screenshot. The one that is marked in yellow color is your IP address.
#5) You can also get to know your IP address in the Charles proxy tool as well. Click on Help => Local IP address, and there you will be able to see a popup with the IP address details.
#6) Open WIFI settings in the mobile and long press on the connected WIFI network.
#7) Click on modify network config.
#8) Click on Show advanced options check box.
#9) Select the Proxy as Manual.
#10) Enter the Proxy hostname with the system IP address and Proxy port as 8888. Click on Save.
#11) As soon as you save the Network settings in your mobile, the Charles proxy tool will display an alert dialog box asking if you want to allow connection from the mobile. Click on the Allow button to continue.
Install Charles Root Certificate On Android Mobile
We need to install Charles root certificate in android as we did on PC.
Follow the below steps to install the root certificate:
The android device needs a screen lock i. pin/pattern or any lock screen. So before proceeding to the further steps make sure that you have set a screen lock.
Open Chrome browser in mobile and enter this URL
It prompts to enter a lock screen password. Enter the password.
The certificate will be downloaded automatically.
Give a proper name when prompted and then save.
Setup is completed now and can monitor the traffic of your mobile in the Charles proxy tool.
If you want to log the traffic only from mobile, then you can disable window proxying from the proxy tool.
Removing Charles Certificate On Android
Enlisted below are the steps involved in Removing Charles Certificate in Android.
You can remove the Charles root certificate from Android when you do not use the Charles proxy tool.
Go to Android device settings and search for Security, there you can find Trusted Credentials.
Find the certificate file with the name given at the time of Certificate installation and delete it.
Charles Proxy Pricing – Subscription Model
Charles proxy tool comes with a freemium model. You can avail of free access to this tool for the first 30 days after installation. After 30 days you need to purchase a license to continue. License pricing ranges from $30 to $700 based on your requirements. For a single license, it costs $30.
In the free access duration, there are some limitations to the below-mentioned points.
#1) There will be some delay after you start the application and it will be visible while opening the tool.
#2) The application stops after 30 min usage. You need to restart the tool to continue.
Frequently Asked Questions
Q #1) Can I configure Charles on my iPhone?
Answer: Yes, you can configure on the iPhone. Please click here to get more details.
Q #2) Which OS versions does Charles support?
Answer: Charles tool can be installed on MAC & Windows PCs and the tool can read the network of Windows/Android/iPhone devices.
Q #3) Is Charles a free tool?
Answer: For the first 30 days after installation, this tool provides a free trial version and after that, you need to purchase a license to continue.
Q #4) Is there any alternative for Charles?
Answer: Yes, MITM (man in the middle) does the same work as Charles. But MITM has very fewer features and is not a friendly user interface.
Q #5) Does Charles support a Web interface?
Answer: Yes, Charles supports the Web interface. You can configure it by creating a credential set (username and password) or can configure it by using an anonymous option. You can find this option in Settings => Web interface settings.
Q #6) Where can I find the official documentation page?
Answer: Click here to visit the official documentation page.
Q #7) How to disable Charles proxy?
Answer: If you want to stop recording, you can click on the Stop record button and you also can close the application. No network call will be logged in the tool. If you uninstall the application, you can remove it from the location where it is installed.
Q #8) What are the Advantages of the Charles Proxy tool?
Answer:
User-friendly UI.
Supports multiple OS versions.
Network throttling Features.
Exporting and importing a session.
Easy to use.
Conclusion
This tutorial explained all about installing and configuring Charles proxy tool. If you have an idea about APIs, Network traffic and Server related knowledge, then it is quite easy to use this tool. Most of the features of this tool are self-explanatory.
Summary:
Charles proxy tool is web traffic debugging proxy.
It helps in debugging/analyzing/testing of web and mobile application traffic logs.
It has easily understandable UI elements.
While configuring, the root certificate installation plays an important role.
Once your work with the tool is completed, it is better to remove the certificate from the PC/mobile.
Hope you enjoyed learning about the Charles Proxy tool.
Frequently Asked Questions about web proxy tools
What is web proxy tool?
A web proxy is a tool that facilitates your connection to a proxy server. Some sites offer a free web proxy to help you connect to their proxy server and browse anonymously. A web proxy browser extension is like a web proxy, but it resides conveniently in your browser, so it’s always there whenever you want to use it.
What is Charles software used for?
Charles Proxy is a web debugging tool that monitors the network calls and decrypts the web traffic. It helps in understanding the content in your network call. E.g. Requests sent to the server and data fetched from the server etc. This network debugging tool can read the web traffic of Windows, Android and IOS devices.Sep 27, 2021
What are common web proxy features?
Proxy Server implements all product features by using the following three services: Web Proxy service Provides caching, cache routing (CARP), support for chains, and reverse proxying. The Web Proxy service supports any client that supports the HTTP protocol.
