What You Don’t Know About the User-Agent – JavaScript in Plain …
3 facts about User-Agent that every developer should knowThere are some facts that I wish I knew before spending half a day digging into a User-Agent issue. I will share what I learnt in this rstly, let’s define what is User-Agent (UA) is a string contained in the HTTP headers and is intended for browser detection: to identify the device/platform of the visiting user, and can be used to determine appropriate content to is a messThe truth is, User-Agent is full of lies. In many cases, a browser pretended to be other browser with User-Agent. In the history of User-Agent, browsers often pretend to be another browser because some websites serve contents(frames, etc) based on the type of browsers like Mozilla. Pretending to be “Mozilla” is the easiest way to receive the contents with now, every browser is disguised as another browser like Mozilla. One example is that Chrome called itself Mozilla/5. 0 (Windows; U; Windows NT 5. 1; en-US) AppleWebKit/525. 13 (KHTML, like Gecko) Chrome/0. 2. 149. 27 Safari/525. 13. Unfortunately, almost all browsers do this, which made User Agent a complete owser detection using UA is not reliableThe User-Agent was commonly used for browser detection, which normally involves searching for a particular string or pattern in the UA string. Below is a simple (dexOf(‘MSIE’) > 0){ alert(‘IE is not supported’);}It’s a quick and easy solution, but it came with a cost. One issue is that the User-Agent string may change in a newer version. Then, the script needed to be updated. If the purpose of UA browser detection is to use/disallow a web feature, it is not practical to find every browser User-Agent, as there are so many variations. A better solution is to use feature detection with a tool like Agent will be deprecated by GoogleIn 2020, Google announced that it is going to “Deprecate and Freeze” User-Agent. “On top of those privacy issues, User-Agent sniffing is an abundant source of compatibility issues, in particular for minority browsers, resulting in browsers lying about themselves, and sites (including Google properties) being broken in some browsers for no good reason, ” said Yoav Weiss, a Google engineer working on the Chrome ’s first step is to deprecate the erAgent method with Chrome 81, then with the release of Chrome 83 in June 2020, the User-Agent string will be freeze with each update. And Chrome 85 will unify the User-Agent across ’s replacement of User-Agent is client ’s much debate and skepticism around Google’s move, but with support from Apple and Microsoft, the phase-out of User-Agent seems nclusionThe following extract from MDN Web sums up the argument of this article ’s very rarely a good idea to use user agent sniffing. You can almost always find a better, more broadly compatible way to solve your problem! If you are not already a paid member of Medium, you can do so by visiting this link. You’ll get unlimited full access to every story on Medium. I’ll receive a portion of your membership fees as a referral.
How to Build a GDPR-Compliant Ad Server | Kevel
Are you looking to build your own ad server? As a publisher, you’ll need to understand GDPR regulations and ensure compliance for your advertisers and European Union (EU) users. If you’re not familiar with the GDPR and its implications, we recommend reading our GDPR and Ad Tech article, as it covers many of the legal details and terms you’ll need to know. This article will present six GDPR considerations for your building process, including how to manage personally identifiable information (PII), how to retain and store data, and how to plan for ongoing risk assessments. Please note: This article is for informational purposes only. Please seek legal counsel to determine how the GDPR affects your business. 1. Understand the PII you collect The first step to building a GDPR-compliant ad platform is understanding the personally identifiable information (PII) you collect and how it’s used. The GDPR regulates the handling of personally identifiable information (PII) for all EU residents that use your web applications, mobile apps, and desktop software. PII is complicated, and you likely collect/store more than you realize. For example, the User Agent string of a web browser can be combined with other data to identify an individual user. Location data for the same user is also considered PII: who else would go from your home address to your work address? Under the GDPR, PII includes, but is not limited to: IP addresses User Agent strings Location data like lat/long and physical addresses Social Security numbers Email addresses Cookie IDs Biometric, financial, behavior, demographic data Mobile IDs (IDFA, AAID, etc. ) Even hashes of this data are considered PII because you can link them to an individual, so there are no workarounds for these concerns – and any fines can be as high as 20M Euros or 4% of your yearly revenue, whichever is higher. The GDPR prohibits using this data in automated decision making (including ad serving) and unsafe storage and leakage of PII. So without EU user consent, you cannot: Send full IP addresses downstream; they must be truncated Pass geolocation data like latitude/longitude to partners Store PII in internal logs, as it might be accessible and viewable to others Below lists some common ways ad servers use PII – and which you should review if you do: Action Consent Required Use a cookie ID or unique user ID for purpose of profiling and user-level targeting Yes, if attributable to an individual Use IDs to track impressions, clicks, conversions, or other engagement metrics Yes Use IDs to regulate ad delivery using frequency capping Yes, as ad views and time stamps on cookies can be tied to specific users Send IP Address or GPS data to a location lookup tool Yes, if you are not truncating the IP Address (like zeroing out the last octet) Store user agent string / location data in a database for purpose of ad delivery, targeting, or storage Yes Send any PII to a downstream ad partner Yes. Any transfer of personal data is subject to strict GDPR rules and may require additional legal documentation. If you’re fielding programmatic requests, you’ll need to send multiple OpenRTB fields downstream. Be sure to read the IAB spec on GDPR first. That said, we don’t expect OpenRTB to ultimately be permissible (court rulings will decide this in the coming years), as the GDPR requires you to inform users what vendors will see the data. Even if you collect consent for sending their PII to, say, Rubicon Project’s ad exchange, you would also need to collect consent to share the user’s PII with all the demand side platforms (DSPs), ad networks, and data providers that Rubicon is integrated with. Given how programmatic advertising works, this is not feasible – and if even one company sees that PII who was not mentioned at time of getting consent, you could be held liable to pay the penalty. 2. Collect consent and honor the data rights You’ll first need a way to collect consent. There are plenty of IAB-certified third-party consent management platforms. You could also build your own CMP using internal code or open-source code from AppNexus or Axel Springer. It should be noted that most CMP implementations are not actually compliant under GDPR, so you should work with your legal team to set up the tools in a compliant manner. Honoring user consent goes well beyond getting the initial “yes”, though. Since cookies can be deleted, you’ll need a persistent way to store who has or hasn’t consented (or you could re-prompt them each time, but that could lead to a poor user experience). Additionally, the GDPR specifies multiple data rights the customer has – including the right to delete their data, the right to see what data you have on them, and the right to rectify it. This means you need a way to store this information tied to a user and easily access/modify it if they request it. (The GDPR does allow you to store PII for the purpose of tracking consent). The quickest way to accomplish this is to store the data in a first-party DMP database like Kevel’s UserDB. This makes PII and consent information retrievable and deletable. Your ad server will also need to reference this database in real time, so you can determine who can or cannot have cookies dropped for each ad request – without slowing down your site. 3. Revisit data retention and storage You will also need to address how you store and back up data. All old data – personal identifiable information (PII) or otherwise – will need to be flushed regularly. Most data breaches are due to old database backups, log files, and even former employee files. One of the biggest mistakes we see companies make is storing PII in their logs. Per the data rights under the GDPR, a user can revoke consent at any time. This becomes more difficult if PII is stored in many places, including raw log files that may be hard or impossible to make changes to. Also, per the GDPR’s right of access, you must be able to tell a EU user all of the information you have for them – so retrieving all of that data from your logs will prove daunting. User data will also need to be stored in a way that allows quick retrieval upon request and prompt removal upon requests to be forgotten. As noted previously, we recommend a first-party database. We recommend transforming your data before logging and storing For example, transform user agent data into high-level form factor data and geolocation data into lower-resolution forms like city, region, and country. This keeps you from inadvertently stepping on EU users’ data rights, including the right to be forgotten and right to access, and it can help you avoid court fees and legal hassles. Kevel’s historic stance on data privacy and security – and the EFF Do Not Track standard – made this easier for our GDPR compliance. You should work with your legal counsel to develop a data retention policy that meets your unique needs. 4. Identify users’ locations in real-time Obviously you’ll need to identify a user’s location in real-time – likely using IP Address, GPS data, or the country they registered an account with – and as needed run it through a reputable location lookup service or database to identify country. Your CMP tool should then prompt consent for anybody in the EU. This includes the United Kingdom, as the GDPR will continue to apply to the UK through the Brexit implementation period (scheduled to end December 31, 2020); the UK will likely adopt a similar law starting in 2021. We also recommended including Switzerland, as it has similar data privacy laws. You may want to play it safe by treating all incoming requests as GDPR-regulated and prompt consent for all users. Kevel allows customers to implement GDPR-compliant features for both EU and global users. 5. Have a risk assessment plan in place Once your server is built, it must be maintained. GDPR compliance requires continuous risk assessment and a vigilant response to data breaches. Depending on your core processing activities, you may also be required to appoint a Data Protection Officer (DPO). As a publisher, you’ll need to conduct regular, recurring risk and vulnerability analyses of your ad platform. We recommend both automated and human-powered analyses to ensure accuracy. You’ll also need a breach notification plan, as you’re required to notify EU users within 72 hours of a breach – and you’re held liable whether or not you were aware of the breach. You may want to additionally obtain PrivacyShield certification to ensure you meet EU data transfer laws. The PrivacyShield framework was designed by the U. S. Department of Commerce and the European Commission to give companies a mechanism for transferring European data to U. companies. This certification is not required by the GDPR but it can demonstrate your due diligence in case of a lawsuit. 6. Update your legal documents There are few steps here. One, you’ll need to update your public Privacy Policy page to provide information on why you collect PII, for what reasons, and more. You can find a template for it here. Two, you’ll want a separate Cookie List page that provides transparency about the cookie names you drop, as well as their lifespan. Finally, your ad server will also require Data Processing Agreements (DPAs) for each of your third-party vendors, as they too must prove GDPR compliance. You’ll need a separate DPA for every service to which you transfer your users’ data, including: Third-party cloud hosting Databases Log hosting Backup services If you’d prefer to have just one DPA, Kevel can help you build your platform and manage these agreements for you! Ready to build a GDPR-compliant platform? As you can see, building a GDPR-compliant ad server is complicated! We hope we’ve taken some of the guesswork out of your planning process. The GDPR has been enforced since May 2018 and continues to evolve with EU court rulings on its interpretation and implementation. To remain GDPR-compliant, you’ll need to follow the legal proceedings from EU member countries and update your ad technology accordingly.
User Agent – Definition, Types, and Importance – Seobility Wiki
Contents
1 Definition
2 Transmitting the user agent through the HTTP header
3 Types of user agents
4 Importance of user agents
5 Related links
6 Similar articles
Definition
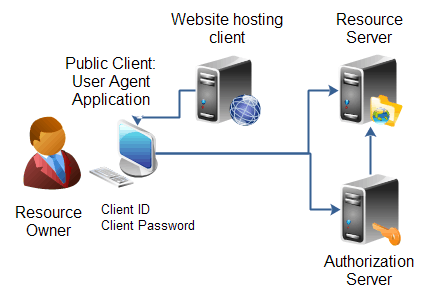
A user agent (short: UA) is software that communicates with servers in a network. An example would be a web browser that retrieves a web page from a server on the internet and displays it. The user agent acts as a mediator between the user and the web server just like a human agent. It processes the user’s instructions, transfers them and receives the requested data. The user agent transmits information such as the browser version, installed plugins, and other data to the web server. Based on this data, the server can assess the capabilities of the user agent and deliver the appropriate data to it.
Figure: User Agent – Author: Seobility – License: CC BY-SA 4. 0
The information that identifies the user agent is transferred to the web server in the HTTP request header. Each header contains a characteristic string that servers can use to identify the application type, operating system, software vendor, or software version of the requesting user agent.
The structure and content of this information are not standardized. Each developer can insert and submit his own information. For example, the basic syntax for a Firefox web browser is:
Mozilla/5. 0 (platform; rv:geckoversion) Gecko/geckotrail Firefox/firefoxversion
Mozilla/5. 0 is a general token stating the web browser is compatible with Mozilla. Modern browsers use this token for historical reasons only, since it is no longer of great importance.
platform describes the native platform the web browser operates on – for example, Windows, Mac, Linux or Android and whether it is a mobile phone or not. Firefox OS for mobile simply puts the word “Mobile” here.
rv:geckoversion indicates the version of Gecko. Gecko is an HTML rendering engine that web browsers use to display a web page. In current browsers, geckoversion is the same as firefoxversion.
Gecko/geckotrail indicates that the browser is based on Gecko. On desktop, geckotrail has the fixed string “20100101”.
Firefox/firefoxversion indicates the browser is a Firefox version with the specified version number.
An example of a Firefox browser on a desktop operating on Windows would look like this:
Mozilla/5. 0 (Windows NT 6. 1; Win64; x64; rv:64. 0) Gecko/20100101 Firefox/64. 0
Information provided by the agent can be modified or falsified. One example would be some mobile web browsers, which can switch between mobile or desktop mode to get access to websites that only allow desktop computers.
In the early days of the internet, Microsoft’s first Internet Explorer pretended to be a Netscape browser to access web pages designed for Netscape Navigator, the dominant browser on the market back then.
Types of user agents
Browsers like Mozilla Firefox, Google’s Chrome as well as Safari and Opera are examples of user agents. However, other applications can also act as user agents. Examples are:
Crawlers: Googlebot, Yahoo! Slurp, MSN bot
Game consoles: PlayStation, Wii, PlayStation Portable and Bunjalloo (the browser on the Nintendo DS)
Legacy operating systems: AmigaVoyager
Link checkers: e. g. W3C-Checklink
SEO tools / on-page crawlers: e. SeobilityBot
Web applications: Flash Player, Adobe Acrobat Reader, feed readers, screen readers, validators, media players, streaming portals
Not all user agents are controlled or instructed by humans. Search engine crawlers are an example of user agents that visit websites automatically.
Importance of user agents
Once a user agent has identified itself to the web server, a process called content negotiation begins. Content negotiation is a mechanism defined in HTTP that allows you to provide different versions of a document or another resource using the same URL. Browsers can specify which version best suits their capabilities with the help of user agent information and request the fitting resource for their needs. A classic application of this mechanism is providing an image in GIF as well as PNG format, and delivering the GIF version to user agents that cannot display PNG images (such as older versions of MS Internet Explorer). Similarly, different stylesheets (CSS), JavaScript, or the mobile version of a web page can be rendered based on browser capabilities. If the user agent transmits the language setting, the appropriate language version of a document can be delivered. A PDF reader can access PDF documents and a media player can access videos.
When an application receives content tailored to its user agent, this process is referred to as agent name delivery. Search engine optimization uses this process to present different content to search engine bots compared to real visitors’ user agents. When this black hat SEO tactic referred to as cloaking is used, visitors see a web page optimized for humans whereas crawlers access content and structure that is mostly simple and optimized for high rankings in search results. However, search engines know this spam technique and therefore often act as browsers.
Similar articles
Proxy Server
Black Hat SEO
Dedicated Server
Frequently Asked Questions about user agent data
What does the user agent tell you?
3 facts about User-Agent that every developer should know The User-Agent (UA) is a string contained in the HTTP headers and is intended for browser detection: to identify the device/platform of the visiting user, and can be used to determine appropriate content to return.Jul 19, 2020
What are the two types of user agent?
User Agent Types: There are two types of user agents: command-driven and GUI- based.
Is user agent PII data?
PII is complicated, and you likely collect/store more than you realize. For example, the User Agent string of a web browser can be combined with other data to identify an individual user. Location data for the same user is also considered PII: who else would go from your home address to your work address?Jan 15, 2020